- September
26, 2015 | Other
-
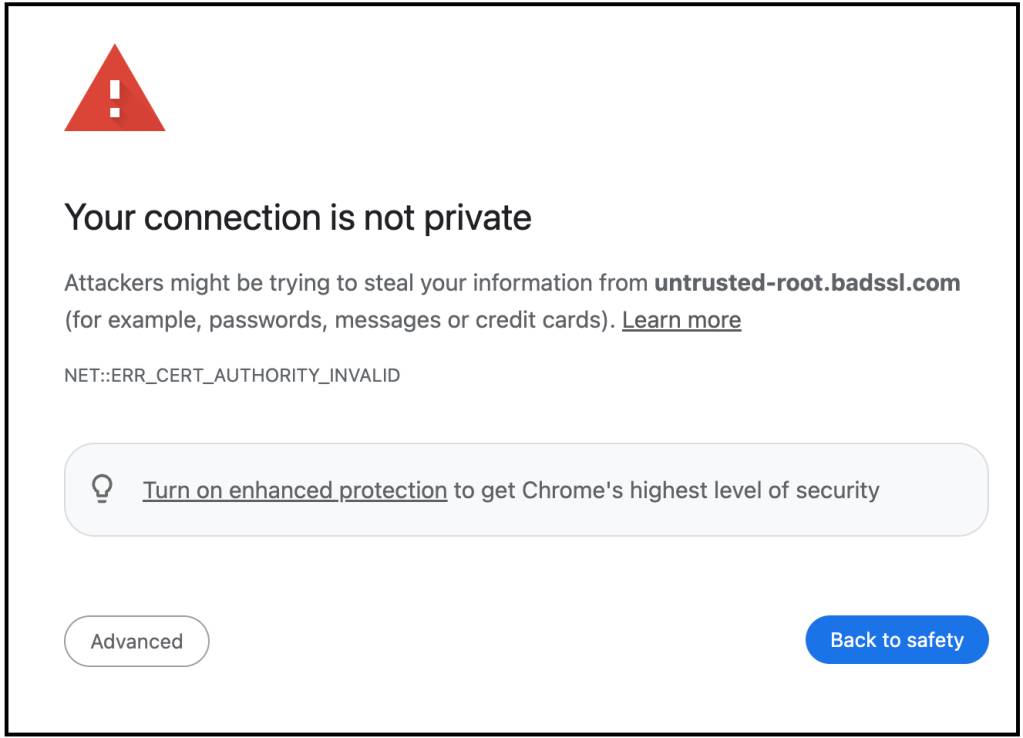
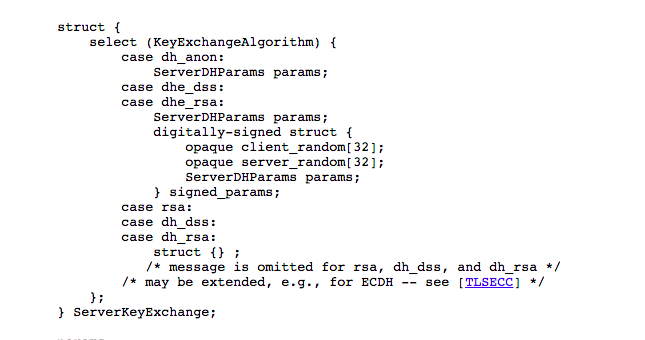
What is export grade cryptography ? Since World War II, many countries including
the U.S., U.K. and others, have regulated the export of cryptography in the
interest of national security till 1992. Those countries used to believe that
they had developed more advanced cryptographic solution than others and they
wished to monitor the communication of other countries and hence restricted the
advanced cryptographic solution to other nations, by their companies.
Restriction had been eased down in 1992 and in 2000 but some are still there.
Only those cryptography solutions which can be breaked by security agencies,
were allowed to export and were known as Export Grade Cryptography. Ciphers
itself are not of Export Grade as they properly follows algorithms. It is the
use of cryptographic keys that are deliberately weekend so that security
agencies can crack them as and when needed. The export-grade encryption had 512
bits, the maximum allowed under U.S. restrictions de...
Continue...