NIC IPv6 DNS Measurement
Measuring who all are querying for nic.in or gov.in domain, what they are querying for and from where they are querying.
NIC had tested its IPv6 connectivity with internet peers on June 8, 2011 (World IPv6 day) and next year on World IPv6 Launch Day (June 6, 2012), we had launched our IPv6 DNS Server (having address 2405:8A00:1000::2) along with some websites. Our IPv6 DNS Servers are live from day one onwards and today we are receiving roughly 54000 queries per hour over IPv6 for various nic.in and gov.in domains.
In this paper, we are showing the following statistics:-
- Who all are querying us
- What they are querying for
- From which part of world we are getting the hits
For taking out the bellow stats, we analyzed 7, 69, 00,000 (roughly 7.7 crore) IPv6 queries.
AS wise Query Statistics
Autonomous System number (ASn) wise query stat gives us the unexpected results. Although we were predicting that Google will be in top 3 but didn’t expect that half of received queries will be from Google only.
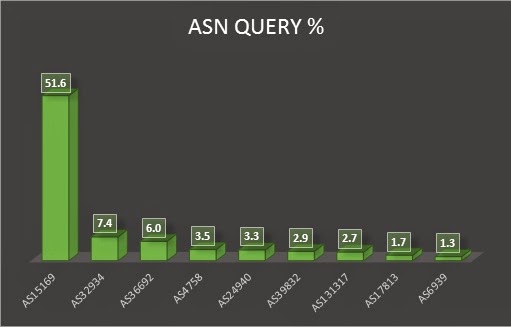
Google tops the list with 51.6% of queries and leads the list with huge margin. Facebook comes 2nd with 7.4% of total queries. Our own AS 4758 comes at 4th place.
|
15169
|
US
|
GOOGLE - Google Inc.,US
|
|
32934
|
US
|
FACEBOOK - Facebook, Inc.,US
|
|
36692
|
US
|
OPENDNS - OpenDNS, LLC,US
|
|
4758
|
IN
|
NICNET-VSNL-BOARDER-AP National Informatics
Centre,IN
|
|
24940
|
DE
|
HETZNER-AS Hetzner Online AG,DE
|
|
39832
|
NO
|
NO-OPERA Opera Software ASA,NO
|
|
17813
|
IN
|
MTNL-AP Mahanagar Telephone Nigam Ltd.,IN
|
|
6939
|
US
|
HURRICANE - Hurricane Electric, Inc.,US
|
|
12008
|
US
|
ULTRADNS - NeuStar, Inc.,US
|
|
7018
|
US
|
ATT-INTERNET4 - AT&T Services, Inc.,US
|
Most unpredictable and still unanswered behavior is having Facebook at number 2nd. I am still wondering why Fb is querying us and that too in that much quantity.
Our own ASn comes fourth after Google, Facebook and OpenDNS. Only 2 organization from India find a place in this list. Apart from NIC only MTNL was able to reach in top 10.
This somehow shows that Indian Internet Users are using Open DNS Servers (like of Google, Hurricane and others).
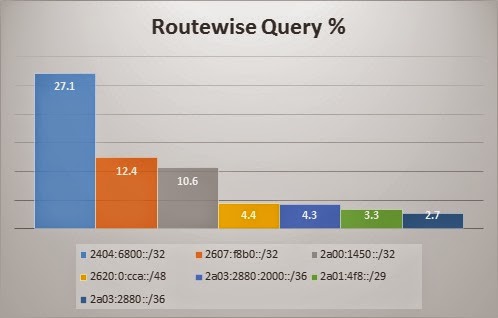
Route wise Query Statistics
Route wise query stats also depicts the same pattern as that of ASn wise. Top 3 segment which queried us the most belongs to Google.
Most Queried Domain
India.gov.in tops in this list. It is the one which was queried maximum number of times over IPv6.
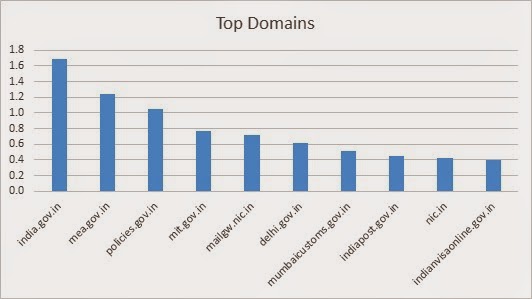
Above graph depicts the top 10 third-level domains among *.nic.in and *.gov.in domain.