DIG is a domain query tool and a part of BIND package of ISC.
Using dig is very simple in Linux but is little bit tricky to use the same in Windows.
I have tried to do the same and sharing you the steps which i follow for configuring the dig in my windows machine.
How to install dig in Windows :-
- Create a folder for dig (eg: C:\dig)
- Download the latest version (currently which is 9.8.5-P2) of BIND software from here (ZIP format)
- Extract the .zip file and copy the dig.* and *.dll files in the folder created in step 1
- Add the folder in the Environment Variables path settings (Right click on My Computer --> click on Properties --> Advance System Settings --> Environmental Variables --> Path )
Use dig more efficiently (using .digrc) :-
dig gives lot of information in its output which may not be useful in most of cases (and may be annoying for some of us). To cut short the dig output to show you only the answer section, you need to give lot of parameters to instruct dig.
C:\Users\kansal>dig india.gov.in any +nostats +nocomments +nocmd +noquestion +recurse india.gov.in. 84 IN AAAA 2001:4408:5200::a464:38bf india.gov.in. 853 IN A 164.100.56.191 india.gov.in. 853 IN NS ns2.nic.in. india.gov.in. 853 IN NS ns1.nic.in. india.gov.in. 853 IN NS ns10.nic.in. india.gov.in. 853 IN NS ns7.nic.in.
Now to give lot of parameters in every query string is not feasible (especially to Windows guys who believe in using mouse more than keyword :) ).
After going through the dig man page, i found a b'ful solution to get rid of entering parameters every time.
Create a file and named it as ".digrc", and add the required parameters in that file. dig command will read the parameters from that file and concatenate the o/p based on the parameters based in '.digrc' file.
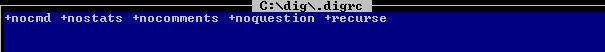
I create a file ".digrc" in C:\dig\ folder. Now the problem is how to tell dig to where to find the .digrc file.
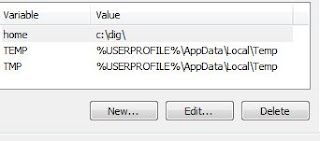
Solution of this is too simple. Just create a 'home' variable and add a value "C:\dig\" for the same.
Now to just check whether everything is working or not as per desired -
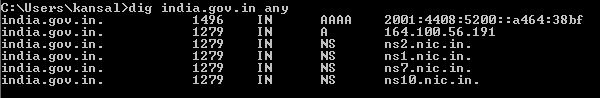
Bingo :) we get the desired output without giving the required parameters.
P.S.-Bind 9.9.5 is the latest version of Bind which is in ESV (Extended Support Version). In this version, normal bind 9.9.5 dig utility wait continuously for indefinite period of time after query through dig command in Windows OS and user have to use Ctrl+C for getting the prompt again. This is a bug in Bind 9.9.5 dig tool which got hits when dig tool is used separately in windows environment (i.e., when only dig tool is used in Windows).
This bug has been rectified in Bind 9.9.5-W1 version which can be downloaded from here.