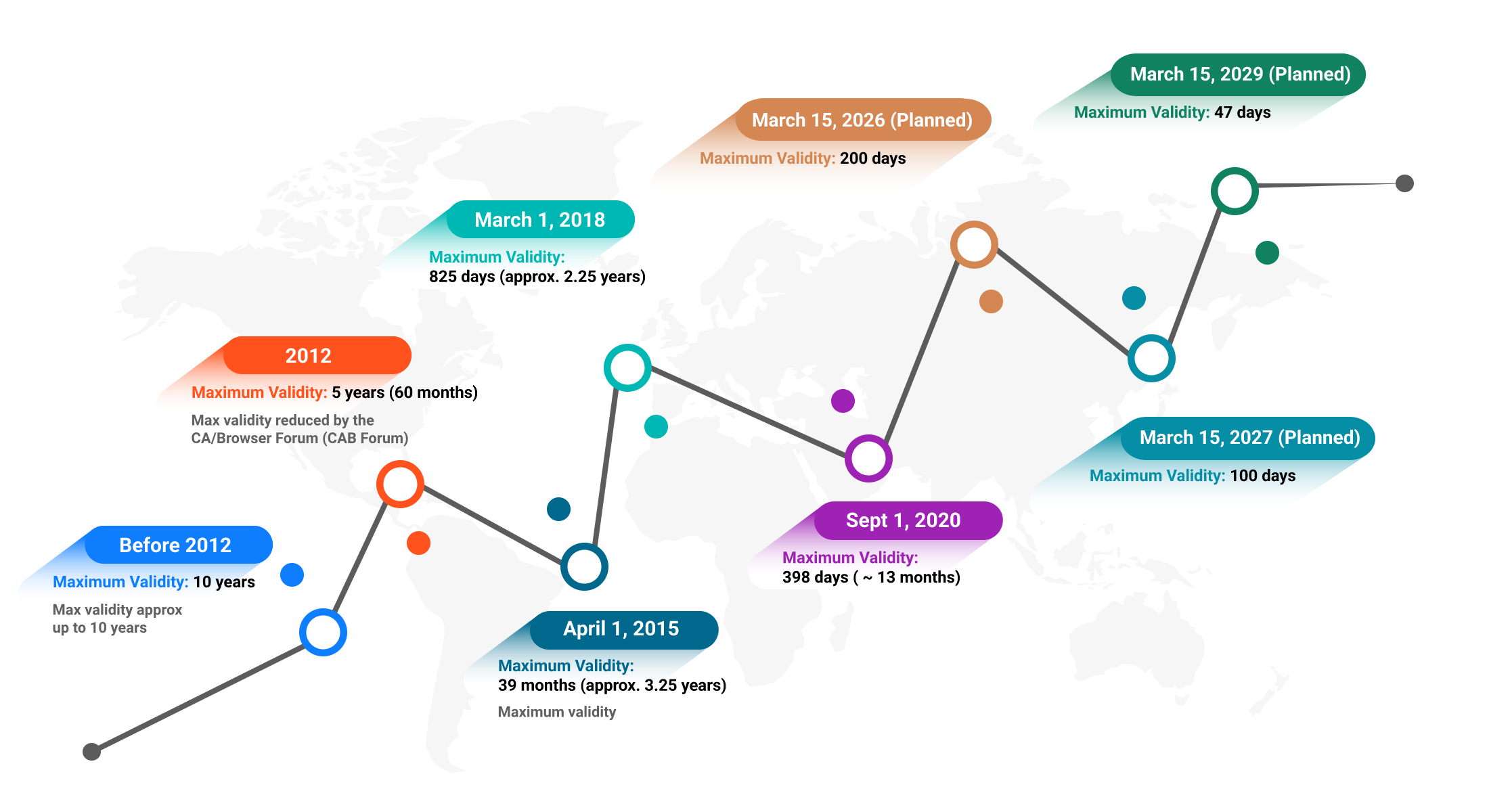
The TLS certificate lifespan is officially set to be drastically reduced to a maximum validity of 47 days by March 15, 2029. This change, approved by the CA/Browser Forum on April 11, 2025, through Ballot SC-081v3 (which has been proposed by Clint Wilson (Apple) and endorsed by Nick France (Sectigo), Ryan Dickson (Google Chrome), and Ben Wilson (Mozilla)) represents a significant shift from the current maximum lifespan of 398 days and is being phased in over several years to improve internet security and encourage automation in certificate management. [1] Voting results on the ballot is covered in the last section of this blog.
Timeline of the Reduction :
Current state (up to March 14, 2026): Maximum certificate validity is 398 days (about 13 months).
398 days = One year (366 for a leap year) + One month (31) + 1 extra dayMarch 15, 2026: Maximum certificate lifespan reduces to 200 days (about 6.5 months), with domain validation reuse also reduced to 200 days.
200 days = 6 months (184 days, considering July to December, or any other combination for covering max days) + half month (15 days) + 1 extra dayMarch 15, 2027: Further reduction to 100 days (about 3.3 months) maximum validity, with domain validation reuse also cut to 100 days.
100 days = 3 months (92 days) + quarter month (7 days) + 1 extra dayMarch 15, 2029: Final enforcement of the 47 days max certificate lifespan (approx 1.5 months), with domain validation reuse dropping to just 10 days.
47 days = 1 months (31 days) + half month (15 days) + 1 extra day
Reasons for the changes
-
Enhanced Security: Shorter certificate lifespans reduce the window of opportunity for attackers to exploit compromised certificates. If a certificate or its private key is compromised, the damage potential is limited to the certificate's shorter validity period. This reduces reliance on often unreliable certificate revocation mechanisms.
-
Improved Cryptographic Agility: Frequent renewals encourage faster adoption of updated cryptographic algorithms and security standards, helping organizations stay resilient against emerging threats, including preparation for quantum-safe cryptography.
-
Reduced Risk of Outdated Information: Long-lived certificates may contain outdated organizational or domain validation information. Shorter lifespans ensure validation data is refreshed more frequently, reducing risks associated with stale or incorrect data.
-
Encouragement of Automation: The increased frequency of certificate renewals (up to 8-12 times per year by 2029) makes manual management impractical and error-prone. This change pushes organizations toward automated certificate life cycle management solutions, which improve operational efficiency and reduce the risk of outages due to expired certificates.
Impact on Organizations
-
Renewal Frequency: Organizations will need to renew certificates roughly twice a year by 2026, quarterly by 2027, and monthly by 2029, increasing operational workload significantly.
-
Validation Reuse Periods: The period during which domain control validation (DCV) and subject identity information (SII) can be reused will also shrink. For example, DCV reuse will drop from 398 days currently to 10 days by 2029, requiring more frequent domain revalidation.
-
Operational Challenges: Manual renewal and validation processes will become untenable. Without automation, organizations face higher risks of service disruption, compliance issues, and security lapses.
-
Cost Considerations: Despite the increased renewal frequency, shorter lifespans do not necessarily mean higher costs. Many providers offer multi-year coverage plans allowing multiple re-issues within the purchased period, helping manage expenses.
Voting Results on Ballot SC-081v3
[2]
Certificate Issuers
30 votes in total:
* 25 voting YES: Amazon, Asseco Data Systems SA (Certum), Buypass AS, Certigna
(DHIMYOTIS), Certinomis, DigiCert, Disig, D-TRUST,
eMudhra, Fastly,
GlobalSign, GoDaddy, HARICA, iTrusChina, Izenpe, NAVER Cloud Trust Services, OISTE
Foundation, Sectigo, SHECA, SSL.com, SwissSign, Telia Company, TrustAsia,
VikingCloud, Visa
* 0 voting NO:
* 5 ABSTAIN: Entrust, IdenTrust, Japan Registry Services, SECOM Trust Systems,
TWCA
Certificate Consumers
4 votes in total:
* 4 voting YES: Apple, Google, Microsoft, Mozilla
* 0 voting NO:
* 0 ABSTAIN: